Hunting Rogue Plan with Meraki API Script
With an API Quickly List and Audit Wi-Fi Rogues on your network
About Rogue Wi-Fi Devices
A rogue Wi-Fi device is any unauthorized device connected to the internal network that broadcasts a wireless SSID without proper approval or oversight. Such devices expand the wireless network footprint without centralized management, bypassing critical security protocols and monitoring.
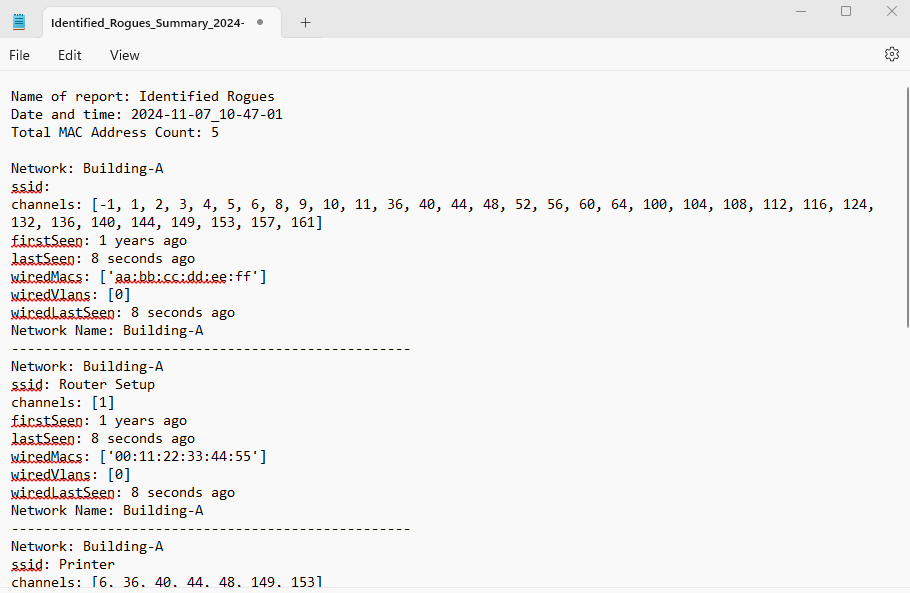
Sample Data
Without visibility into these rogue devices, several risks emerge. It becomes difficult to evaluate the device’s security measures and to gauge its potential impact on the stability and integrity of the wired network. Rogue devices can act as entry points for unauthorized access, introducing vulnerabilities that compromise sensitive data.
Additionally, rogue Wi-Fi devices can interfere with managed wireless infrastructure, causing service degradation for authorized users. By operating on overlapping channels or frequencies, these devices introduce signal interference, which reduces network performance and disrupts connectivity for users who depend on reliable wireless access.
To mitigate these risks, it is essential that all wireless devices are authorized and managed by the network security team. This ensures robust security, reliable network performance, and protection of digital assets.
Mitigation
Addressing rogue Wi-Fi devices effectively requires a clear workflow and policy. When handling rogue devices in a tactical manner, there are multiple approaches available. For example, using Ekahau heatmaps can help approximate device locations, while NetAlly offers detection tools. Additionally, APIs such as those available with Meraki allow quick identification of rogue Wi-Fi devices directly from the platform.
Below is an example of an API script written to list rogue devices for an organization on the Meraki platform. This link to a script produces terminal data and generates three files for tracking and managing rogue devices:
Merakicode/RogueAirMarshall_SupportingFiles at main · jadexing/Merakicode
Spreadsheet of Rogue Device Data
Useful for demonstrating the scale of rogue devices to management.Text File with Terminal Output
Serves as a checklist to guide mitigation efforts.Spreadsheet with Rogue Device Counts
Summarizes the number of rogue devices detected on the network.
Thanks for checking out my blog and taking this journey with me. If you have some tips on the subject, I’d love to hear them. Find me on X @jamiegprice CWNE #510